By Robert McMurray
March 28, 2014
Introduction
For Internet Information Services (IIS) 7.0 on Windows Server® 2008, Microsoft released a separate, downloadable WebDAV extension module that was completely rewritten. This new WebDAV extension module incorporated many new features that enable Web authors to publish content better than before, and offered Web administrators more security and configuration options. With the release of IIS 7.5, support for a newer WebDAV module was built-in for Microsoft IIS, and Microsoft released an updated version of the downloadable module that had been released for IIS 7.0. This newer version of the WebDAV module provides shared and exclusive locks support to prevent lost updates due to overwrites.
This document walks you through adding WebDAV publishing to an existing Web site by using the new WebDAV user interface and by directly editing the IIS configuration files.
Note: This walkthrough contains a series of steps in which you log on to your Web site using the local loopback address and the local administrator account. When using an administrator account, these steps should only be followed on the server itself using the loopback address or over SSL from a remote server. If you prefer to use a separate user account instead of the administrator account, you must create the appropriate folders and set the correct permissions for that user account when necessary.
IN THIS WALKTHROUGH
- Prerequisites for Installing and Configuring WebDAV on IIS
- Installing WebDAV on IIS 7.0
- Installing WebDAV on IIS 7.5
- Installing WebDAV on IIS 8.0 and IIS 8.5
- Enabling WebDAV Publishing by using IIS Manager
- Enabling WebDAV Publishing by editing the IIS configuration files
Note: This topic discusses using the WebDAV Redirector to connect to your web site. Please see the Using the WebDAV Redirector topic for more information; specifically the “Troubleshooting the WebDAV Redirector” section if you have trouble using the WebDAV redirector.
Prerequisites for Installing and Configuring WebDAV on IIS
The following items are required to complete the procedures in this article:
- IIS 7.0 or later must be installed on your server, and the following must be configured:
- The Default Web Site that is created by the IIS 7.0 installation must still exist.
- The Internet Information Services Manager must be installed.
- At least one authentication method must be installed.
Note: If you choose to use Basic Authentication with the WebDAV redirector, you must connect to your server using HTTPS.
- The WebDAV Redirector must be installed for Windows Server 2008, Windows Server 2008 R2, or Windows Server 2012. (The WebDAV Redirector is already installed on Windows Vista, Windows 7, and Windows 8.) To install the WebDAV Redirector, use Server Manager to install the Desktop Experience feature.
Installing WebDAV on IIS 7.0
DOWNLOADING THE RIGHT VERSION FOR YOUR SERVER
There are two separate downloadable packages for the new WebDAV extension module; you need to download the appropriate package for your version of Windows Server 2008:
- 32-bit Installation Package:
- 64-bit Installation Package:
LAUNCHING THE INSTALLATION PACKAGE
You must run the installation package as an administrator. This can be accomplished by one of the following methods:
- Logging in to your server using the actual account named “Administrator”, then browsing to the download pages listed above or double-clicking the download package if you have saved it to your server.
- Logging on using an account with administrator privileges and opening a command-prompt by right-clicking theCommand Prompt menu item that is located in the Accessories menu for Windows programs and selecting Run as administrator, then typing the appropriate command listed below for your version of Windows to run the installation:
- 32-bit Windows Versions:
- msiexec /i webdav_x86_75.msi
- 64-bit Windows Versions:
- msiexec /i webdav_x64_75.msi
- 32-bit Windows Versions:
WALKING THROUGH THE INSTALLATION PROCESS
- When the installation package opens, you see the following screen. If you agree to the license terms, check the “I accept” box, then click Install.
- The progress indicator will reflect the status of the installation as it proceeds.
- After the installation has completed, click Finish.
- The WebDAV extension module is now installed.
Installing WebDAV on IIS 7.5
IIS 7.5 FOR WINDOWS SERVER 2008 R2
- On the taskbar, click Start, point to Administrative Tools, and then click Server Manager.
- In the Server Manager hierarchy pane, expand Roles, and then click Web Server (IIS).
- In the Web Server (IIS) pane, scroll to the Role Services section, and then click Add Role Services.
- On the Select Role Services page of the Add Role Services Wizard, expand Common HTTP Features, select WebDAV Publishing, and then click Next.
- On the Confirm Installation Selections page, click Install.
- On the Results page, click Close.
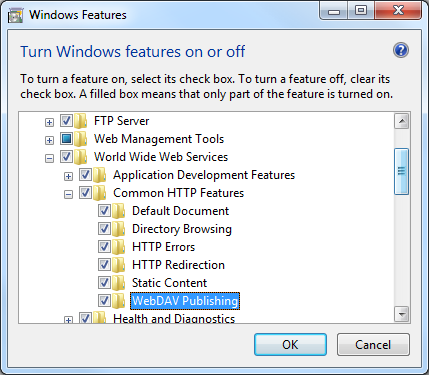
IIS 7.5 FOR WINDOWS 7
- On the taskbar, click Start, and then click Control Panel.
- In Control Panel, click Programs and Features, and then click Turn Windows Features on or off.
- Expand Internet Information Services, then World Wide Web Services, then Common HTTP Features.
- Select WebDAV Publishing, and then click OK.
Installing WebDAV on IIS 8.0 and IIS 8.5
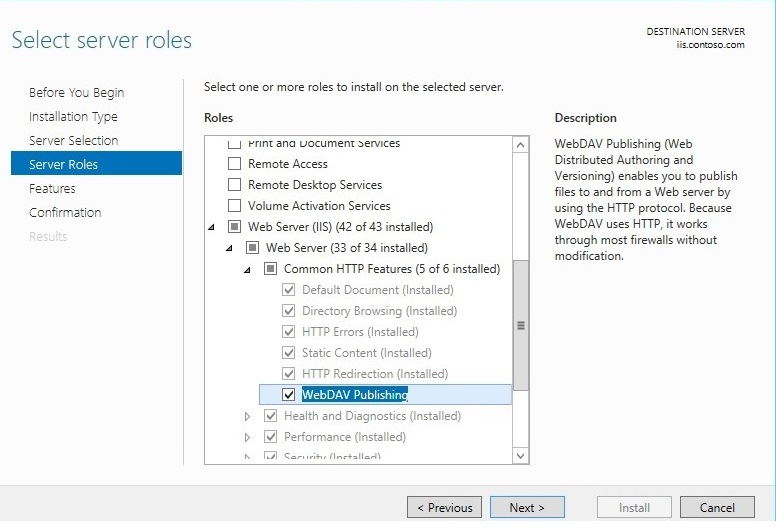
IIS 8.0 ON WINDOWS SERVER 2012 AND IIS 8.5 ON WINDOWS SERVER 2012 R2
- Click the Server Manager icon on the desktop.
- In the Server Manager window, click the Manage menu, and then click Add Roles and Features.
- On the Before You Begin page, click Next.
- Select the Installation Type and then click Next.
- Select the Destination Server, and then click Next.
- On the Select Role Services page, expand Web Server (IIS), expand Web Server, expand Common HTTP Features, and then select WebDAV Publishing. Click Next.
- On the Select Features page, click Next.
- Confirm the installation selection, and then click Install.
- On the Results page, verify that the installation succeeds, and then click Close.
- On the Confirm Installation Selections page, click Install.
- On the Results page, click Close.
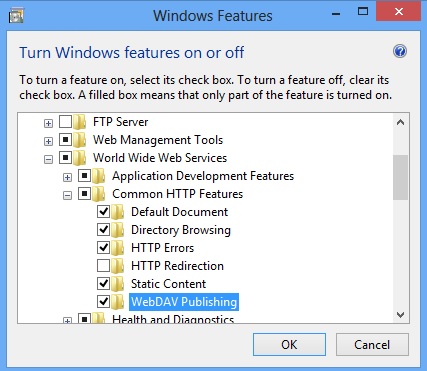
IIS 8.0 FOR WINDOWS 8 AND IIS 8.5 FOR WINDOWS 8.1
- On the taskbar, hold down the Windows key, and then press the X key. Click Control Panel.
- In the Control Panel, click Programs and Features, and then click Turn Windows Features on or off.
- Expand Internet Information Services, then World Wide Web Services, then Common HTTP Features.
- Select WebDAV Publishing, and then click OK.
Enabling WebDAV Publishing by Using IIS Manager
The WebDAV extension module makes it easy to add WebDAV publishing to existing sites by providing you with a wizard that walks you through all of the required steps.
Note: The following procedure is performed using IIS 8.5 on Windows Server 2012 R2
STEP 1: ENABLING WEBDAV AND ADDING AN AUTHORING RULE
In this first step, we add WebDAV publishing to the Default Web site, and add the required settings to allow the local administrator account to edit the content.
- In IIS Manager, in the Connections pane, expand the Sites node in the tree, then click the Default Web Site.
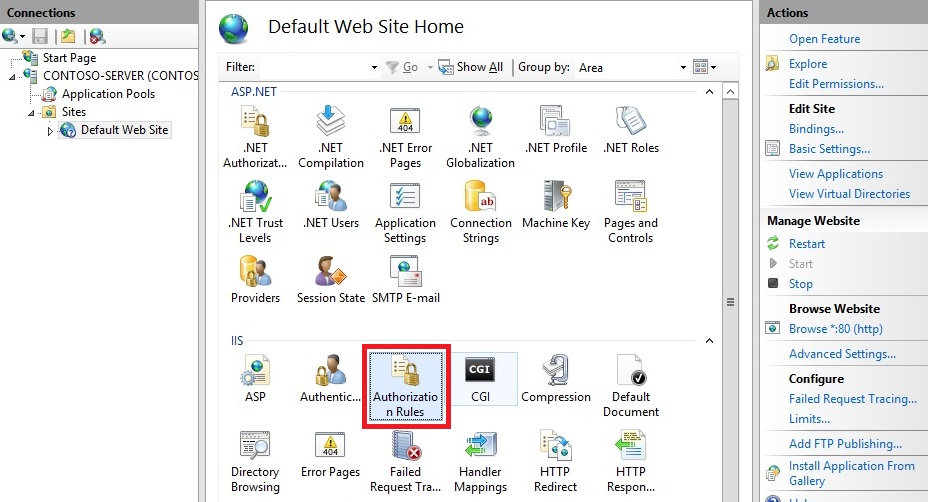
- As shown in the image below, double-click the WebDAV Authoring Rules feature.
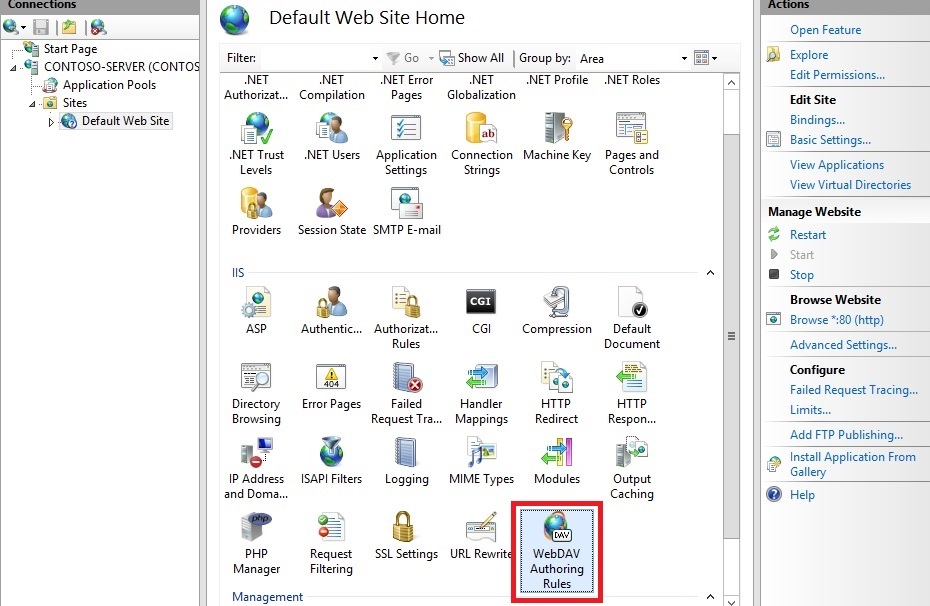
- When the WebDAV Authoring Rules page is displayed, click the Enable WebDAV task in the Actions page.
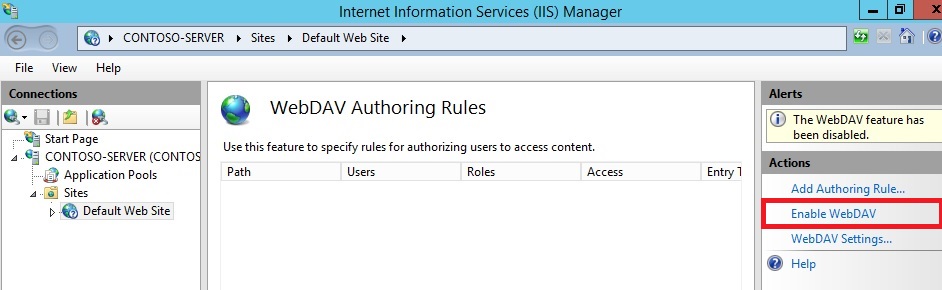
- Once WebDAV has been enabled, click the Add Authoring Rule task in the Actions pane.
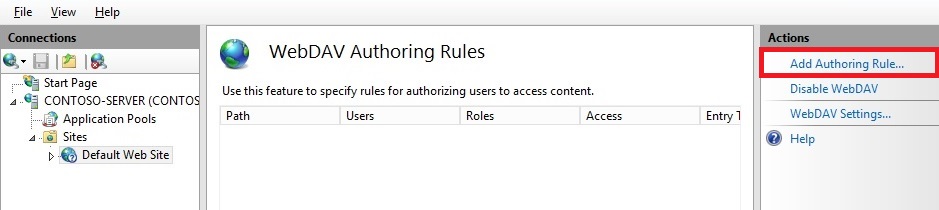
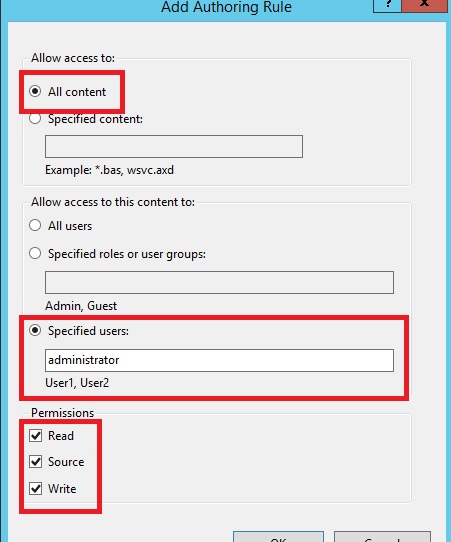
- When the Add Authoring Rule dialog appears:
- Click All content to specify that the rule applies to all content types.
- Choose Specified users and type “administrator” for the user name.
- Select Read, Source, and Write for the permissions.
- When you have completed these items, click OK.
Summary for enabling WebDAV authoring and adding an authoring rule
Task completed. You have enabled WebDAV authoring on an existing Web site.
To recap the items that you completed in this step, we added WebDAV publishing to the Default Web Site by:
- Enabling WebDAV for the Web site.
- Adding an Authoring Rule for the local administrator account for Read, Source, and Write access.
Note: As mentioned earlier, your default request filtering settings may block several file types from WebDAV authoring. If you do not modify your request filtering settings, you may see various errors when you try to publish files that are blocked. For example, if you attempt to upload or download a web.config file you will see errors in your WebDAV client. For more information about configuring your request filtering settings, see the How to Configure WebDAV with Request Filtering walkthrough.
STEP 2: LOGGING IN TO YOUR WEBDAV SITE
In Step 1 above, you enabled WebDAV publishing for your Default Web Site and added an authoring rule for the local administrator account for Read, Source, and Write access to your Web site’s content. In this step, you log in using your administrator account.
Ensuring that you have authorization and authentication configured
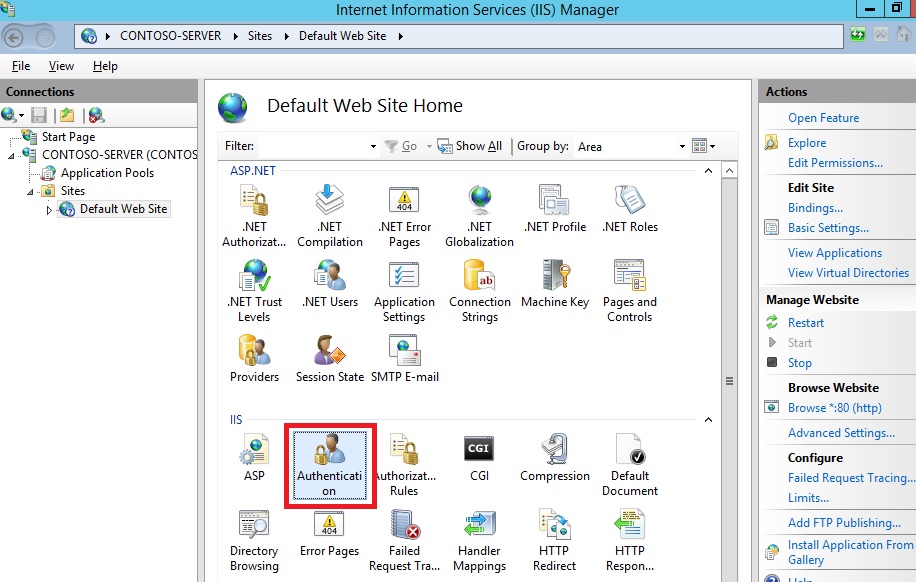
- In IIS Manager, in the Connections pane, expand the Sites node in the tree, then click the Default Web Site.
- Double-click the Authentication feature.
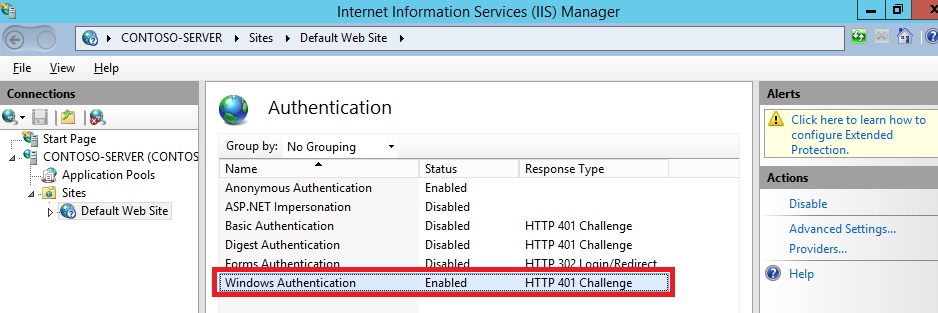
- When the Authentication feature opens, make sure that Windows Authentication is enabled. If it is not enabled, selectWindows Authentication, and click Enable in the Action menu.(Note: You can use Basic Authentication with WebDAV, but the WebDAV redirector will only use Basic authentication with SSL connections.)
- In IIS Manager, click the Default Web Site under the Sites node in the tree.
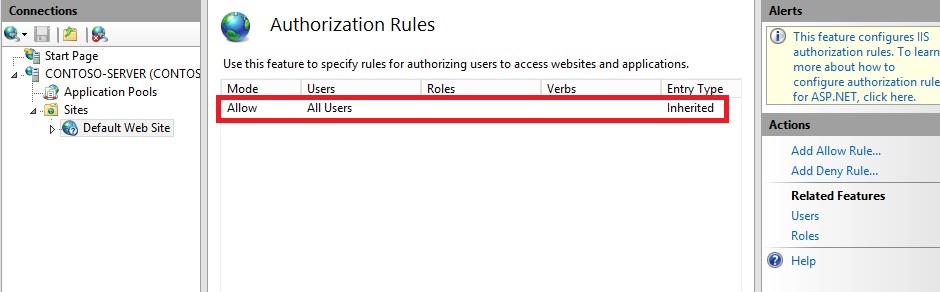
- Double-click the Authorization Rules feature.
- When the Authorization feature opens, make sure that an Allow rule is defined that includes the administrator account. (For example, the default rule for IIS allowing access to All Users will include the administrator account.)
Logging in to your WebDAV site using your administrator account
Logging into your WebDAV site requires the WebDAV Redirector. The WebDAV Redirector is used to publish content to an existing Web site that has the WebDAV nodule installed. You must use Server Manager to install the Desktop Experience feature before you can use the WebDAV redirector. For more information, see Using the WebDAV Redirector.
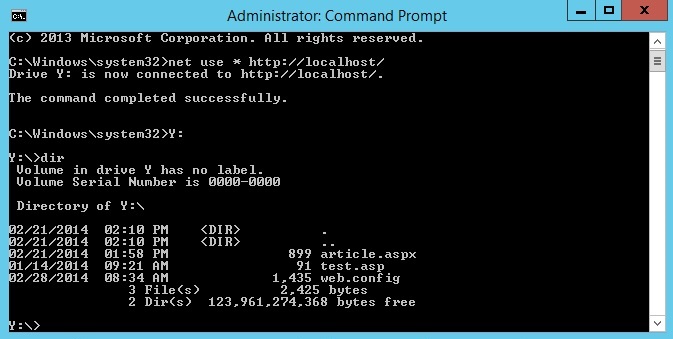
- On your WebDAV server, open a command prompt session.
- Type the following command to connect to your WebDAV server:
net use * http://localhost/
You now have a drive mapped to your WebDAV-enabled web site using the local administrator account, and based on the authorization rule that we added in Step 1, you have Read, Write, and Source access to the content folder.
 Summary for logging into your WebDAV site
Summary for logging into your WebDAV site
To recap the items that you completed in this step:
- You verified that your Web site had sufficient authentication and authorization settings.
- You logged in to your WebDAV site as the local administrator.
Enabling WebDAV Publishing by Editing the IIS Configuration Files
You can also add WebDAV publishing to an existing Web site by editing the IIS configuration files.
Note: Editing your applicationHost.config file requires full administrative permissions. This is best accomplished using one of two methods:
- Log in to your computer using the local “administrator” account.
- If you are logged in using an account with administrative permissions that is not the local “administrator” account, open Notepad using the “Run as Administrator” option.
Note: The above steps are required because the User Account Control (UAC) security component in Windows Server 2008 and later will prevent access to your applicationHost.config file. For more information about UAC, please see the following documentation:
The following steps will walk you through all of the required settings to add WebDAV publishing for the Default Web Site.
- Using a text editor such as Windows Notepad, open your applicationHost.config file, which is located in your %SystemRoot%\System32\inetsrv\config folder by default.
- Scroll to the bottom of your applicationHost.config file and locate the <location> section for your Default Web Site that contains your authentication settings. If this section does not exist, you must add it. This should resemble the following example:
<location path=”Default Web Site”>
<system.webServer>
<security>
<authentication>
<anonymousAuthentication enabled=”true” />
<basicAuthentication enabled=”false” />
<digestAuthentication enabled=”false” />
<windowsAuthentication enabled=”true” />
</authentication>
</security>
</system.webServer>
</location> - Make sure that you have Windows authentication method enabled.
- Add a <webdav> section beneath the closing </authentication> tag that will contain your WebDAV settings.
- Add an <authoring enabled=”true” /> element to the <webdav> element
- Add an <authoringRules> collection with a single entry for <add users=”administrator” path=”*” access=”Read, Write, Source” />.
- Your Default Web Site’s settings should now resemble the following example:
<location path=”Default Web Site”>
<system.webServer>
<security>
<authentication>
<windowsAuthentication enabled=”true” />
<anonymousAuthentication enabled=”false” />
<digestAuthentication enabled=”false” />
<basicAuthentication enabled=”false” />
</authentication>
</security>
<webdav>
<authoring enabled=”true” />
<authoringRules>
<add users=”administrator” path=”*”
access=”Read, Write, Source” />
</authoringRules>
</webdav>
</system.webServer>
</location> - Save your applicationHost.config file.
You should now be able to log in to your WebDAV-enabled site using a WebDAV client using the administrator account, but no other users should be able to access the content using WebDAV.
Summary for adding WebDAV publishing by editing the IIS configuration file
In this task, you added WebDAV publishing to your Default Web Site by editing the IIS configuration files. To recap the items that you completed in this task:
- You enabled Windows Authentication for the Default Web Site.
- You enabled WebDAV for the Default Web Site.
- You added a WebDAV authoring rule for the administrator account with Read, Write, and Source access to the Default Web Site.






 Back to the top
Back to the top









 PeterW
PeterW Note
Note



